
A global view: Themes for risk leaders in financial services to build Resilience by Design
Tags
Across resilience domains, regulations are coming in thick and fast, with the Digital Operational Resilience Act (DORA) being one of the most impactful. Taking a smart approach to the ever-evolving regulatory landscape is no mean feat for global financial services organisations.
In resilience there are regulations covering resolution, business continuity, third-party risk management, and data privacy. There are some consistent themes across the regulations, such as prioritising important business services for customers, but often, they are nuanced in either language or requirements. So, what are the common themes in resilience regulation that we can use as a baseline to build a framework?
Mapping dependencies
The mapping of dependencies features across several key regulations, such as the UK’s Operational Resilience policy, the Monetary Authority of Singapore guidelines, and the EU’s DORA. Mapping is usually focused around understanding what resources across people, premises, technology, data, and third-party organisations need to operate for their customer facing services.
- By using existing resources such as Business Impact Assessments and data mapping to inform resilience mapping, the process can be expedited and aligned to existing documentation.
- Having a common approach and shared terminology supports the identification of critical resources across the business. It also allows the business to respond to multi-jurisdictional regulations. For example, having a clear inventory of resources to support your resilience planning can support data mapping, business continuity, resolution planning, and outsourcing resilience.
- By using a consistent approach, mapping will act as a baseline for response to any new or evolved regulatory measures. However, for larger organisations this can be difficult, as at times, understanding the full operating environment is a larger than large task. By putting the work in now, businesses can set themselves up to build resilience across domains and jurisdictions.
Criticality and concentration risk
By mapping dependencies, organisations will likely understand what critical resources underpin external and internal services. But what next? Financial services regulations are becoming ever more focused on understanding criticalities and concentrations across the sector. DORA, the UK’s proposed Critical Third-Party legislation, MAS’s Business Continuity Management Guidelines, and forthcoming US regulations all reference concentration risk as a key theme.
Regulators are focused on Cloud Service Providers (CSPs) and firms can implement a multi-vendor strategy, or utilise multiple availability regions/zones as potential ways to increase resilience through substitutability and redundancy. But don’t forget critical services, such as data providers, or sector wide tech firms that underpin key services. While CSPs are an important area to build resilience, speaking with peers and understanding from your third party if they provide a critical service across the sector shouldn’t be forgotten.
- Consider geographic concentration risk. Are resources located in one geographic region? This could impact an organisation’s cloud strategy when reviewing availability zones, data strategies for storing collected personal data, and remote access or flexible working strategies when reviewing personnel availability.
- Understanding where data is stored and what systems are used to transfer data is key to understanding what systems need to be protected, and where contracts need to be reviewed if using a third party. Understanding data flows across the business supports businesses in understanding where critical data is stored, where data processing is occurring with third parties, and where technical controls need to be hardened, or legal controls reviewed.
Incident reporting
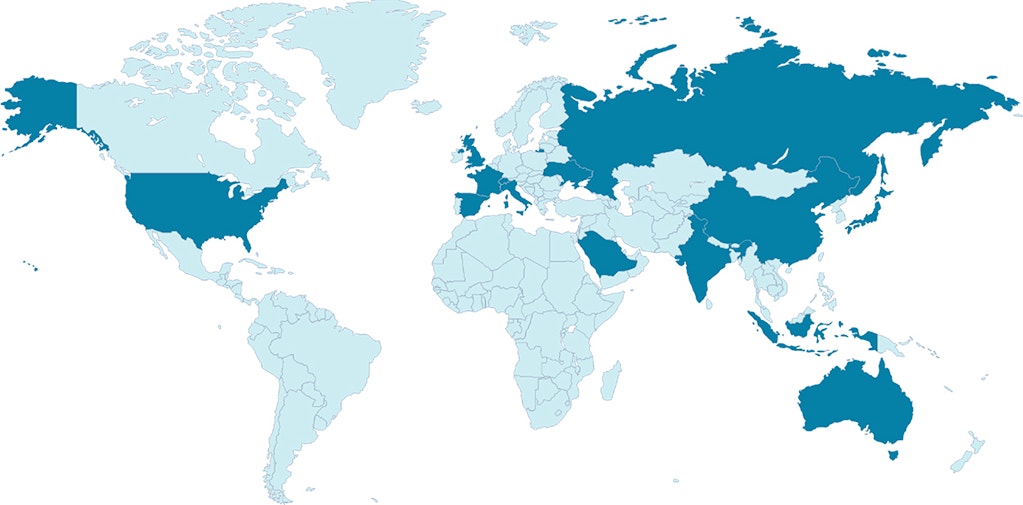
Reporting operational incidents to regulatory bodies is common across jurisdictions. But many authorities have nuanced requirements. The map below shows what jurisdictions have cyber incident reporting requirements. These authorities have differing thresholds, reporting timelines, and required information.
- There is an increasing focus across jurisdictions on reporting personal data breaches. Currently, under GDPR, EU personal data breaches that meet a certain threshold must be reported to the relevant European Supervisory Authority (ESA) within 72 hours. US states are moving towards requiring notification, but with varying thresholds, and in Asia-Pacific, different jurisdictions require breach notifications. Using tooling to set thresholds for incident reporting can support businesses in working towards a stop clock for notification that can be tailored depending on the region.
- Standardised operational incident taxonomies do not currently exist in any operationalised way. A prominent requirement of DORA is that ESAs will set templated reporting guidelines for organisations to meet. Anticipating what requirements will be, and setting up tools to support centralised reporting should be a focus over the next 12 months. This includes being able to understand the impact and root cause of incidents, which at times can be difficult to quantify.
- Incident planning is a core feature of operational resilience, with global regulations requiring organisations to have incident and communications plans in place to respond to operational disruption. Businesses can use time out of crisis to develop and rehearse plans for response, so they become second nature, and seek to understand where strengths within their business lie to deal with different crisis scenarios. Using leadership training to understand personalities in a crisis can evidence to the regulators that the firm are training leadership to understand the importance of responding to disruption to limit impact to the market and customers.
Exercising
Testing resilience contingencies is not new and features in recognised international standards such as ISO23001. However, regulatory requirements around exercising now mandate firms must test their resilience against ‘severe but plausible’ scenarios.
- Regulations such as DORA and MAS’s BCM guidelines encourage firms to exercise across the sector and to share threat intelligence across peers. Firms of all sizes should look to share information on how to manage operational disruption and in-the-moment notification of potential threats. How they do this to maintain confidentiality can be a hard line to tread, but using collective action groups, such as the FSCCC or AFME can be a great place to start.
- Aligning exercising schedules with third-party reviews can also enhance a firm’s understanding of both their reliance on the third party, but also where there may be substitutable resources. Scenario testing with a third-party provider is a requirement of DORA, but can also be treated as an extension of a firm’s due diligence process, by using an exercise to truly understand a third party’s resilience arrangements.
- Exercising allows for clear alignment with a firm’s risk management framework, testing your IBSs against known risks in your taxonomy will support an overall alignment between your risk and resilience teams but also allow for a more tailored experience for your firm, rather than an out-of-the-box exercise experience.
Resilience regulatory requirements and industry standards are ever evolving. Firms more than ever need to understand what regulatory requirements they need to adhere to and how new technology, people, premises, third parties, and data resources can impact their alignment with regulations. By getting a reasonable grounding in the basics outlined above, firms can be set up for success to respond to an exciting new operating landscape. An example we recently saw was firms using Generative AI to iterate products, but with those small product focused teams not realizing that the technology may mean they are out of compliance with data privacy laws, or that the product/service becomes reliant on a new third-party data source. By integrating these elements of resilience by design (inclusive of privacy and security by design) into existing work practices, firms can continue to align with regulatory requirements while continuing to innovate.
Map data source: Financial Stability Board: Recommendations to Achieve Greater Convergence in Cyber Incident Reporting Final Report
Explore more







